 Wumbo
Wumbo
I run window manager and to make removable devices show up in gui filemanager i putted this in my xinitrc file: if which dbus-launch >/dev/null && test -z "$DBUS_SESSION_BUS_ADDRESS";
then
eval "$(dbus-launch --sh-syntax --exit-with-session)"
fi
i'm already using exec ck-launch dbus-launch --sh-syntax --exit-with-session in my xinitrc
 Wumbo
Wumbo
https://gnix0.wordpress.com/2018/09/07/access-android-devices-in-freebsd-11/
i'll try. thank you
 Anonymous
Anonymous
i'm already using exec ck-launch dbus-launch --sh-syntax --exit-with-session in my xinitrc
I have not actually tried it myself with an android device, might try it tomorrow!
 neb
neb
https://www.thezdi.com/blog/2020/9/1/cve-2020-7460-freebsd-kernel-privilege-escalation
Patching time
 neb
neb
also very interesting is the distribution to be found here: https://bsdstats.org/bt/releases.html
It means all the older releases are vulnerable!
 Anonymous
Anonymous
Some one could help me to find the file where a video is cached while you're watching on Firefox? I'm trying using lsof but it still has too much information
 neb
neb
Seriously @Jharked999 ur annoying as fuck. In leaving this forum because of u
Use the block button?
 neb
neb
 Anonymous
Anonymous
Hey could anyone ask Admin of hardenedbsd group to unblock me?
I am immediately banned after joining and posting question link.
 Anonymous
Anonymous
Hi my friends I'm trying to research about VPN's. My goal is to connect my phone device to my free BSD computer and then navigating through a tunnel reaching a website
 Anonymous
Anonymous
I think it is possible but FreeBSD forums explain how to but the connection is made between my device on my os computer acting as the ending node
 Anonymous
Anonymous
Hi pals. I want you give me a minute for asking some information about security
Do you need to know all checklist items? Could take much longer then ... 😉
 Anonymous
Anonymous
Truth is, if you want to 'secure any server' (Windows/Linux/Unix), serious business, so to say, you end up examining/verifiy/configure a few thousand switches/items
 Anonymous
Anonymous
Here, politicians can show up to public audiences, any chat from either WhatsApp or SMS. I read that governments like Russia, sells software for exposing WhatsApp information. Israel widely offers through a private company the same service. I accept the principle where nothing is totally secure. But when you live in the middle of a criminal state, you loose progressly the calm.
 Anonymous
Anonymous
There are many ways to catch your privacy, but when the state leads up these cyber crime, the most wising is to protect yourself
 Anonymous
Anonymous
And the second point of this little exposition is how to dealing with active and passive rules for decreasing this risk
 Anonymous
Anonymous
Get a copy of TAILS (4.10, I believe), burn the iso to DVD and surf with it, when you want to check on sth seriously
 Anonymous
Anonymous
Even a little RaspberryPi is way better than nothing. Low power devices with 2x Ethernet LAN are better, though...
 Anonymous
Anonymous
Of course, it could. Only, you must be a real pro to get it configured in way, that is really safe.
 Anonymous
Anonymous
And what if you connect through VPN to your Freebsd server and the server acts like a bridge connecting two different sites?
 Anonymous
Anonymous
With each separate instance of a device you gain automatically way more security, than you could achieve by (mis-)configuring only one single computer, you have to rely on
 Anonymous
Anonymous
Already good, but it's not enough in my opinion. I've been sitting here now for months dealing with network security ... it is really complex. I do not trust ANY operating system. The more I look into the differences between different Linux distros, the more I learn, that nobody seem to have serious interest to make your computing experience rocksolid in terms of IT-security. Lot of work needs to be done... in the end you regularly run out of lifetime, due to lack of knowledge...
 Anonymous
Anonymous
That holds also true for the BSDs, I believe. You only know, when you have touched every aspect of the whole OS.
 Anonymous
Anonymous
And what if you connect through VPN to your Freebsd server and the server acts like a bridge connecting two different sites?
Thus, Firewall and Antivirus are also important.
 Phil
Phil
And the second point of this little exposition is how to dealing with active and passive rules for decreasing this risk
- First be sure that you have encrypted all disk with full disk encryption with algorithm like aes (and not des)
- For communication remember : "today we kill on metadata" - vice president NSA. In fact communicate with encryption method and hide the communication (you can use tor for it). The problem with WhatsApp is when one of the interlocutors enable sync with Google cloud (there exist an article about this on internet)
- be aware of your physical security
 Phil
Phil
- for asymmetric encryption avoid the eleptic curve NIST-P256 (it's backdoored by NSA and it's a known fact)
 Anonymous
Anonymous
I'm personally still far away from full encryption. You need huge knowledge for doing so. Nobody teaches you. As I've said earlier: no organisation has the slightest interest in teaching you those computing skills.
 Anonymous
Anonymous
ive got one of these coming in the vain hope that it will lead me to find some sort of use for kubernates
 Anonymous
Anonymous
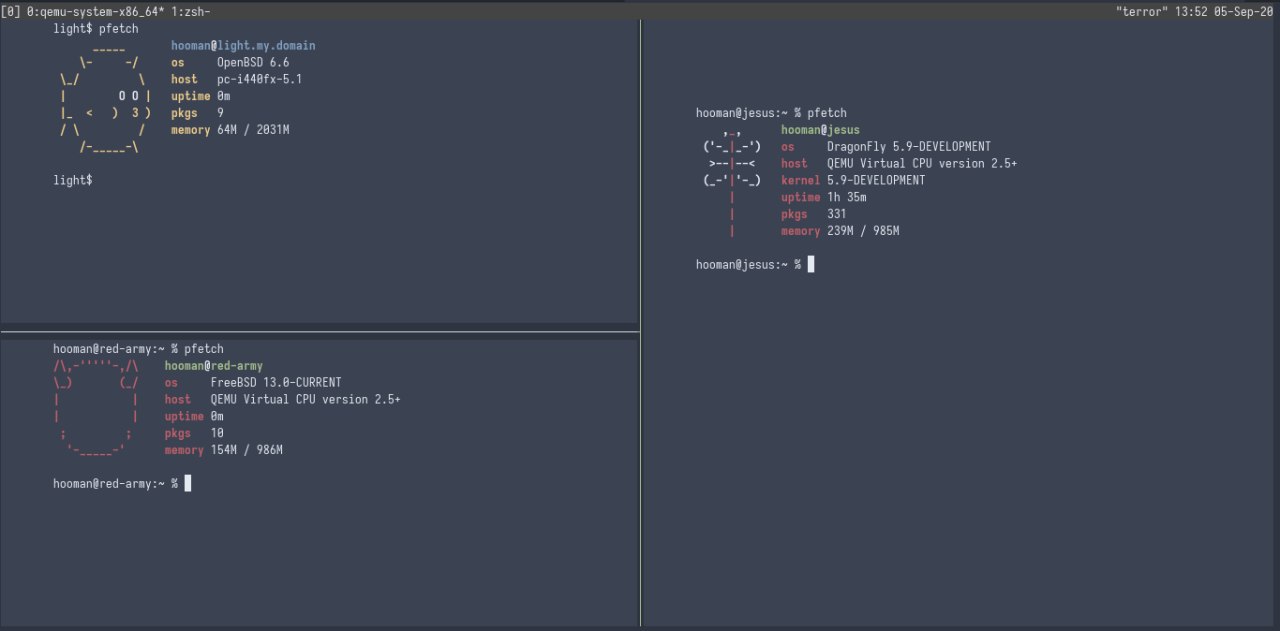
Two QEMUs running in (an old) OpenBSD, 6.6!!) Muchas coolos 😎
no
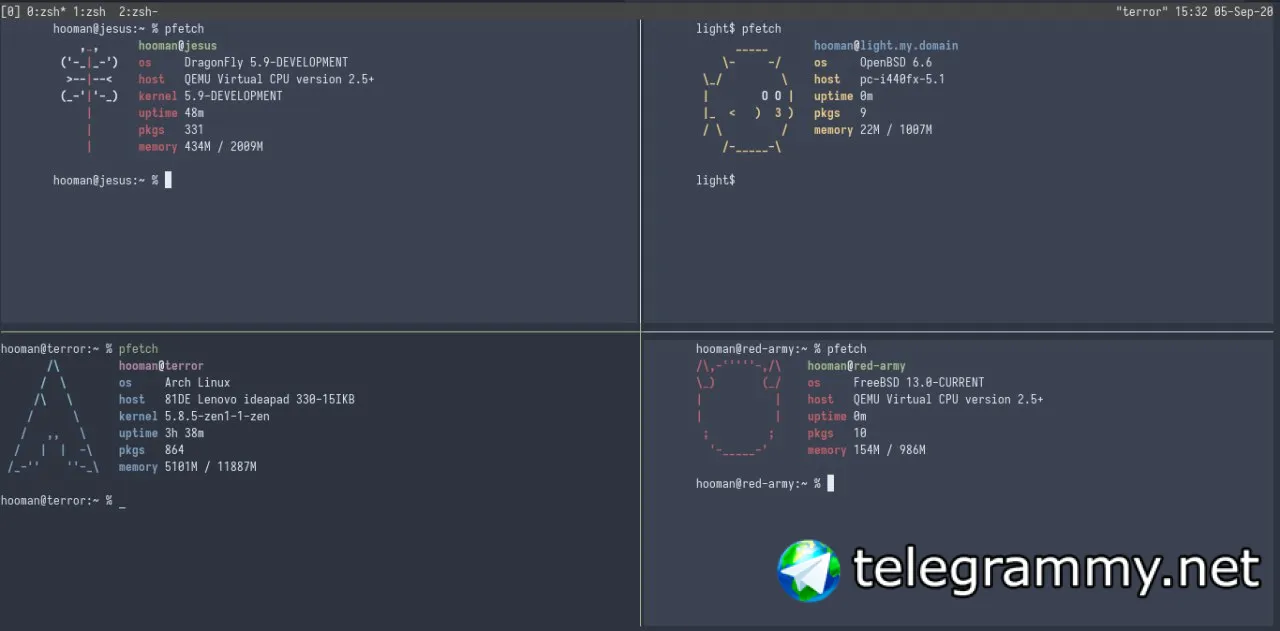
three QEMU's on an arch install


 ɴꙩᴍᴀᴅ
ɴꙩᴍᴀᴅ
 kub-kun
kub-kun

